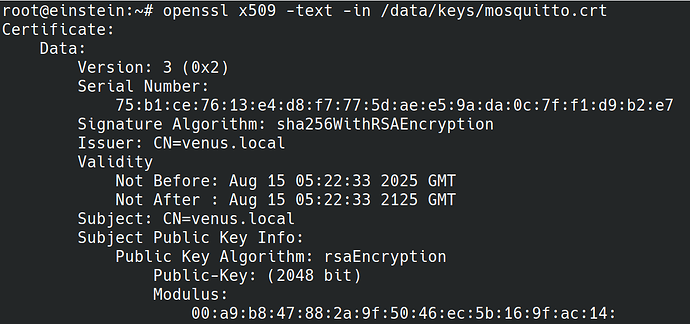
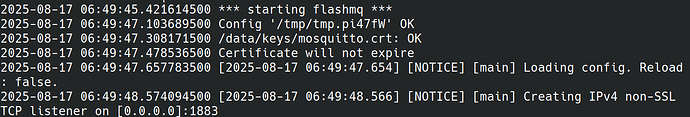
Yes sure.
Right now they full with the same 3 lines, repeated every few minutes. I closed the browser window that was connected straight to the Cerbo, and have had no new messages since.
I am pretty sure when I looked yesterday there were other messages as well, but those old files are gone by now. I’ll have another look tomorrow to see if anything else gets added now that I don’t have webui open.
@4000000068a30430372c4a5c [2025-08-18 10:44:54.925] [NOTICE] [main] Accepting connection from: address='127.0.0.1',
transport='TCP/Websocket/Non-SSL', fd=19
@4000000068a304303827a21c [2025-08-18 10:44:54.941] [NOTICE] [T 0] Client '[ClientID='guiv2a7d284e2c8738fcd', userna
me='', fd=19, keepalive=60s, transport='TCP/Websocket/Non-SSL', address='127.0.0.1', prot=3.1, clean=0]' logged in s
uccessfully
@4000000068a304a607a0df8c [2025-08-18 10:46:52.127] [NOTICE] [T 0] Removing client '[ClientID='guiv2a7d284e2c8738fcd
', username='', fd=19, keepalive=60s, transport='TCP/Websocket/Non-SSL', address='127.0.0.1', prot=3.1, clean=0]'. R
eason(s): Browser navigating away from page, socket disconnect detected
@4000000068a304a937d9d03c [2025-08-18 10:46:55.936] [NOTICE] [main] Accepting connection from: address='127.0.0.1',
transport='TCP/Websocket/Non-SSL', fd=19
@4000000068a304a9386bdedc [2025-08-18 10:46:55.946] [NOTICE] [T 0] Client '[ClientID='guiv2e03aa8e066c7cd21', userna
me='', fd=19, keepalive=60s, transport='TCP/Websocket/Non-SSL', address='127.0.0.1', prot=3.1, clean=0]' logged in s
uccessfully
@4000000068a3051f0590c054 [2025-08-18 10:48:53.092] [NOTICE] [T 0] Removing client '[ClientID='guiv2e03aa8e066c7cd21
', username='', fd=19, keepalive=60s, transport='TCP/Websocket/Non-SSL', address='127.0.0.1', prot=3.1, clean=0]'. R
eason(s): Browser navigating away from page, socket disconnect detected
@4000000068a30522386eccdc [2025-08-18 10:48:56.946] [NOTICE] [main] Accepting connection from: address='127.0.0.1',
transport='TCP/Websocket/Non-SSL', fd=19
@4000000068a30522396c012c [2025-08-18 10:48:56.963] [NOTICE] [T 0] Client '[ClientID='guiv2877bd2186e743528', userna
me='', fd=19, keepalive=60s, transport='TCP/Websocket/Non-SSL', address='127.0.0.1', prot=3.1, clean=0]' logged in s
uccessfully
@4000000068a3059808a105c4 [2025-08-18 10:50:54.143] [NOTICE] [T 0] Removing client '[ClientID='guiv2877bd2186e743528
', username='', fd=19, keepalive=60s, transport='TCP/Websocket/Non-SSL', address='127.0.0.1', prot=3.1, clean=0]'. R
eason(s): Browser navigating away from page, socket disconnect detected
@4000000068a3059b37955ccc [2025-08-18 10:50:57.932] [NOTICE] [main] Accepting connection from: address='127.0.0.1',
transport='TCP/Websocket/Non-SSL', fd=19
@4000000068a3059b388e91ac [2025-08-18 10:50:57.946] [NOTICE] [T 0] Client '[ClientID='guiv29a2fae4b58b66b43', userna
me='', fd=19, keepalive=60s, transport='TCP/Websocket/Non-SSL', address='127.0.0.1', prot=3.1, clean=0]' logged in s
uccessfully