Good morning!
In 2021 I shared details of our Bluetooth GATT protocol. Which works for a few products.
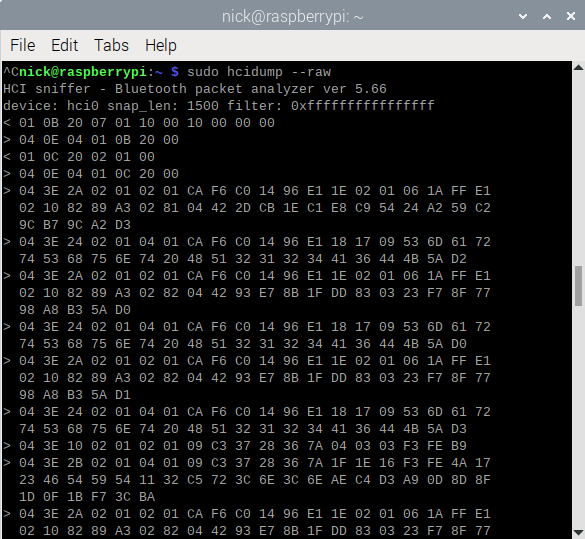
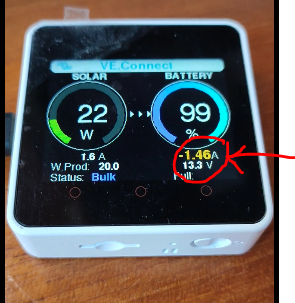
Since then we came up with what I think is a better idea for 3rd party integration for read-out, which is using BLE advertising data, sometimes also referred to as BLE Broadcasting.
Thats the same mechanism behind what we commercially call “Instant read out over BLE”. Full Victron product compatibility list is here in the manual for the VictronConnect App.
This message is to share the protocol PDF of that more widely.
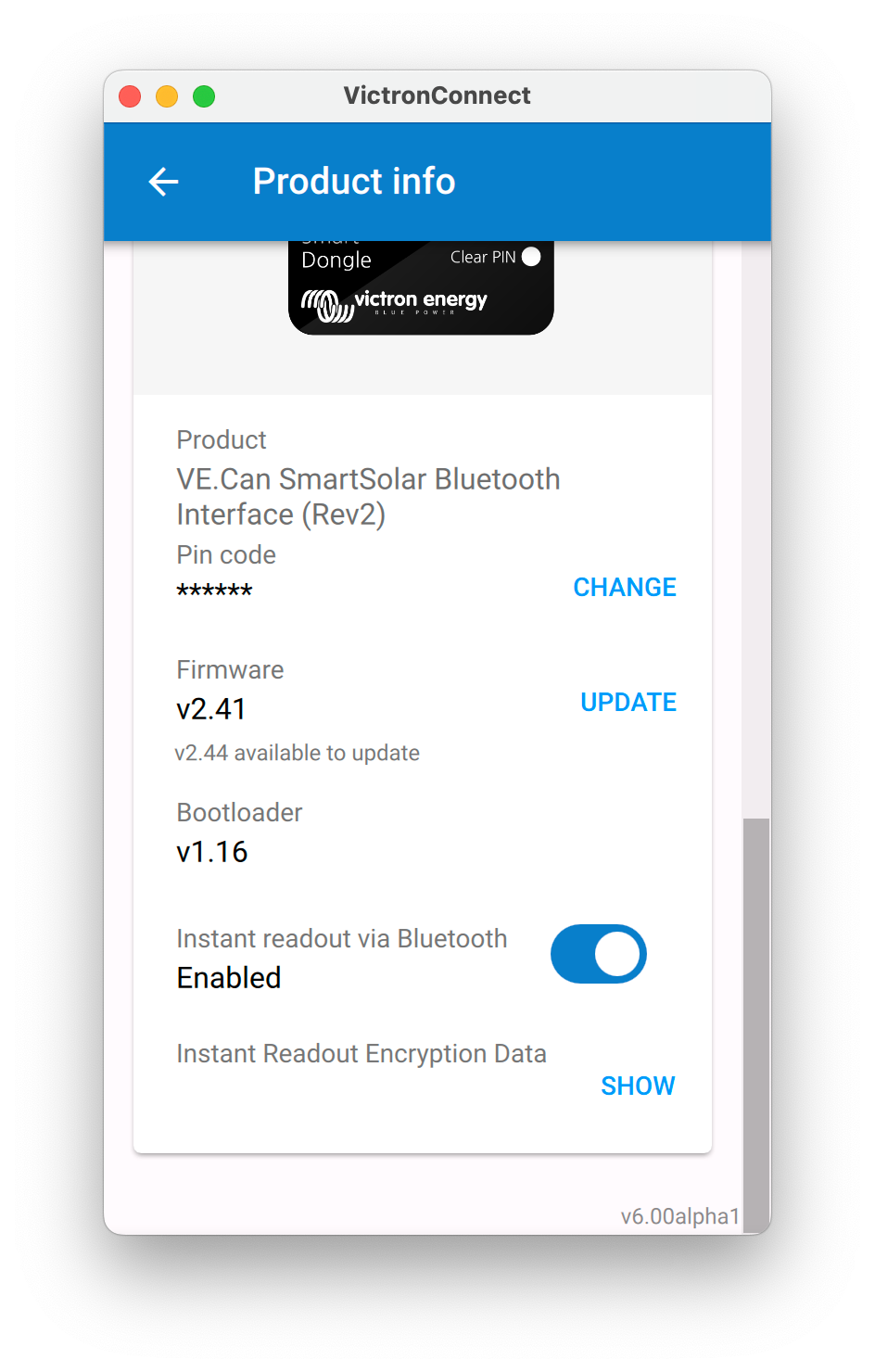
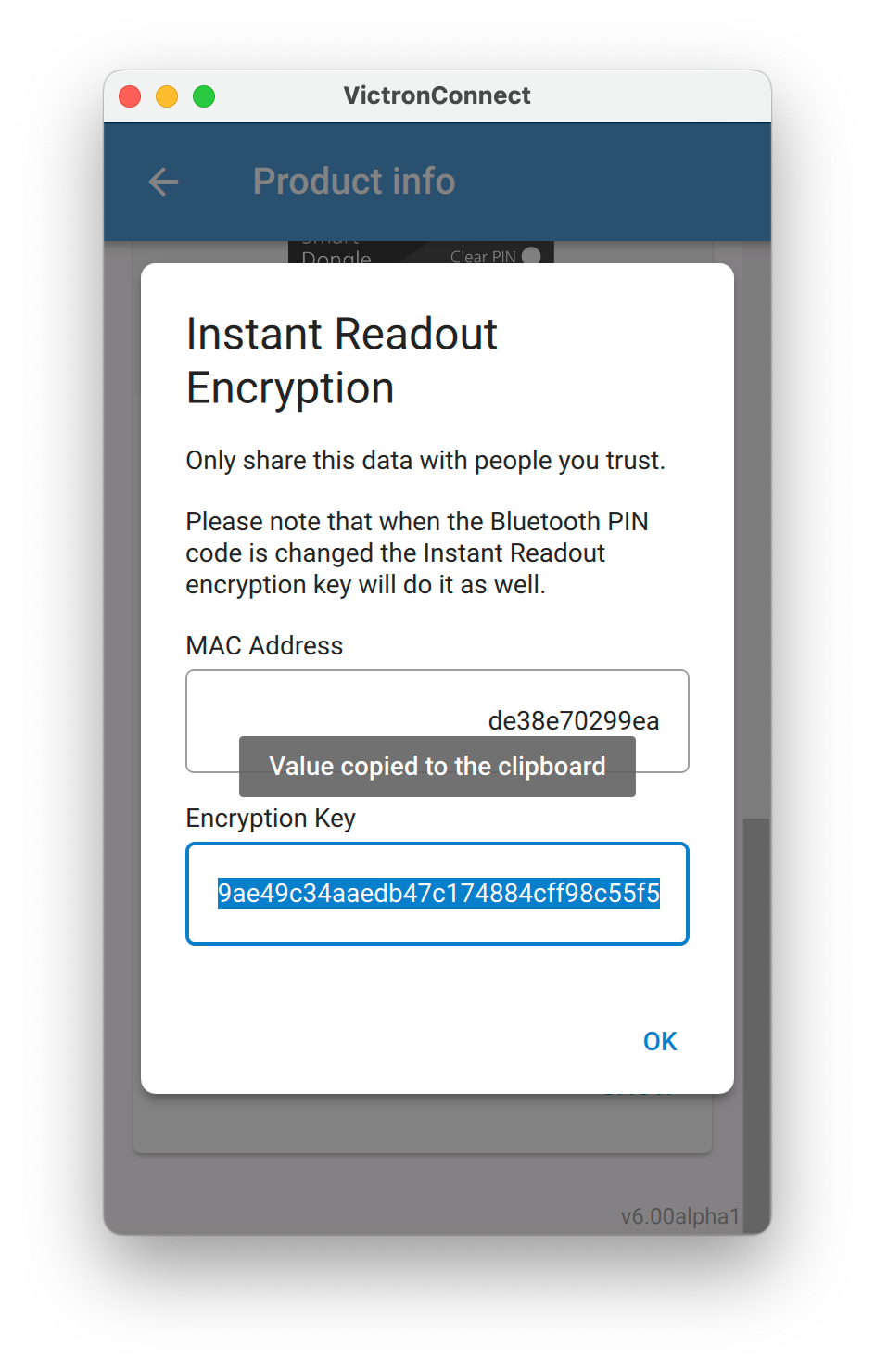
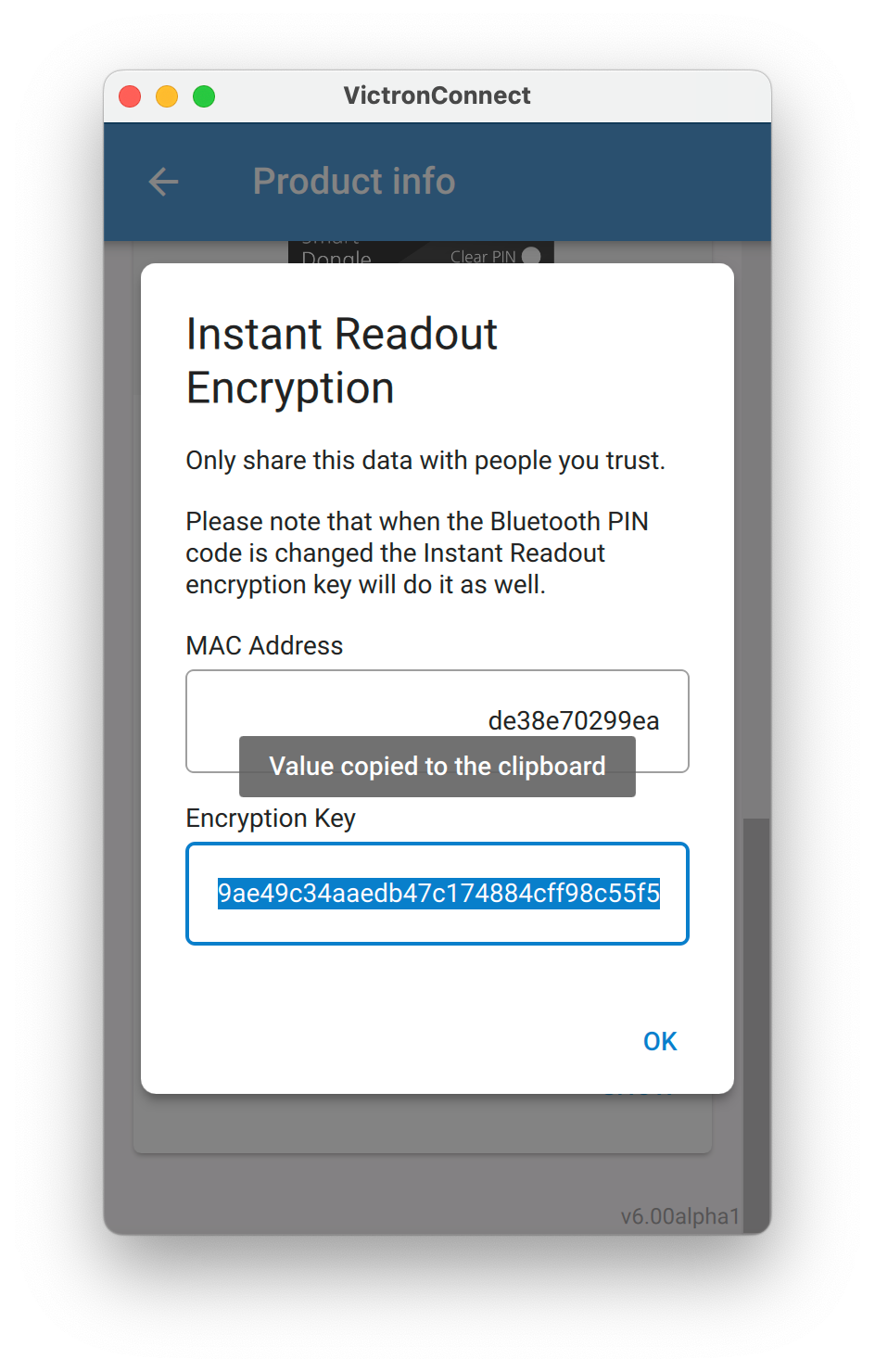
To use this data, you need to get your hands on the encryption key. It can be copied from VictronConnect, see my answer below with a few screenshots on where to find that.
Alternatively, there is a trick to look into VictronConnect files on your computer. As documented by @netsrac27: in Library/Application Support/Victron Energy/Victron Connect you'll find a file called "Victron Connect.sqlite". Inside of this database you'll find a table called "advertisementKeys". It lists MAC address of the sensor and the advertising key. So there is a way to extract the encryption key from that database.
I’m quite sure that there is already code published by people that takes advantage of this.
Have a good weekend!
Matthijs
extra_manufacturer_data - 2022-12-14.pdf